DEPRECATION WARNING
This documentation is not using the current rendering mechanism and is probably outdated. The extension maintainer should switch to the new system. Details on how to use the rendering mechanism can be found here.
EXT: LDAP Integration¶
| Author: | Kasper Skårhøj |
|---|---|
| Created: | 2002-11-01T00:32:00 |
| Changed: | 2005-08-19T01:13:52 |
| Author: | Norman Seibert |
| Email: | seibert@entios.de |
| Info 3: | |
| Info 4: |
EXT: LDAP Integration¶
Extension Key: eu_ldap
Copyright 2000-2002, Norman Seibert, <seibert@entios.de>
This document is published under the Open Content License
available from http://www.opencontent.org/opl.shtml
The content of this document is related to TYPO3
- a GNU/GPL CMS/Framework available from www.typo3.com
Table of Contents¶
EXT: LDAP Integration 1
Introduction 1
What does it do? 1
Screenshots 1
Users manual 2
FAQ 3
Adminstration 4
How authentication works 4
Known problems 4
LDAP support in PHP 4
Configuration of BE-users 4
ChangeLog 4
Version 2.0.9: 4
Version 2.1.4: 4
Version 2.2: 4
Version 2.2.2: 4
Introduction¶
What does it do?¶
This extension enables import/update/deletion of frontend-users from a LDAP-directory, especially W2k actice directory. In this way, TYPO3 can be used as an intranet CMS. Department information can be used to join users to corresponding usergroups.
For each sysfolder holding users multiple LDAP servers can be defined.
Users manual¶
Installation¶
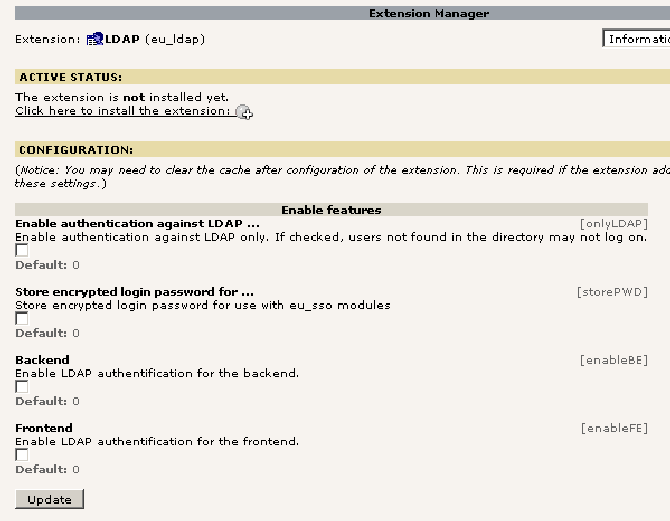
When you click the extension in the extension manager you may activate some basic (reads: not dependent on a server definition) features of the extension. For instance you may restrict authentication to your directory without a fallback against the TYPO3 user database.
The default settings prevent the extension to do anything! You have to activate it for the frontend and backend separately!
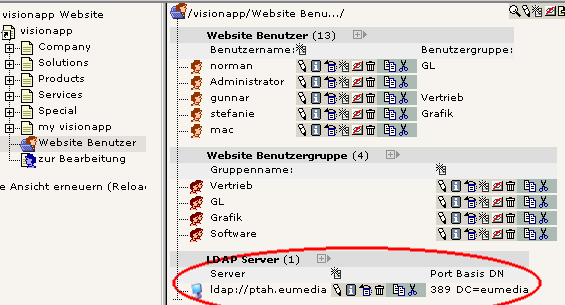
Creation of servers and users¶
To create FE-users and LDAP servers follow the following steps:
Define a SysFolder for storing your FE-users.
When you use the LDAP attribute “department” you can create corresponding usergroups in the SysFolder. A user in the department “Software” for example will then be joined the group “Software”. This way you can apply access rules on pages and content elements depending on the department.
Create a new LDAP server in the above mentioned SysFolder by choosing “new” and selecting “LDAP server”. Fill in the appropriate parameters for your organization.
You may create multiple LDAP servers per SysFolder.
Click on “LDAP Integration” in the “web” section and choose the above mentioned SysFolder. You should see a short summary with the numbers of users both in TYPO3 and in the directory.
Now choose an option from the dropdown menue. You may import new users, update the existing ones (without importing new ones!) or delete users without a corresponding entry in the directory.
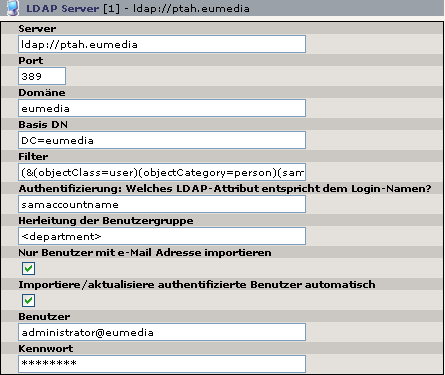
Server¶
c
Port:¶
a
Port:
b
389
c
Optional
Domain:¶
a
Domain:
b
eumedia
c
Used for authentication purposes, "loginname" -> "domain\loginname"
Base DN:¶
a
Base DN:
b
DC=eumedia
c
Filter¶
a
Filter
b
(&(objectClass=user)(objectCategory=person)(samaccountname=<search>*) )
c
Searchfilter for the LDAP query, <search> is replaced by the users's loginname
Server type:¶
a
Server type:
b
c
Active Directory does not fulfill the X.500 standard when doing authenticated binds. To authenticate your FE-users against the directory you must set the server type correctly.
User:¶
a
User:
b
???
c
Optional, user must be allowed to search LDAP directory
Password:¶
a
Password:
b
********
c
Use memberOf-Attribute¶
a
Use memberOf-Attribute
b
c
Active Directory (and NDS as far as I know) extends the LDAP standard by an attribute “memberOf”. For each group the user is a member of, this attribute is added holding the group's DN.
When the box is checked the user's groups are evaluated by using this attribute and the next parameter “build usergroup” is ignored.
Build usergroup¶
a
Build usergroup
b
<division>_<department>
c
Optional, when set the user is assigned the group resulting from the given LDAP attributes.
Suppose you have a user in the division “Seattle” and department “Production”. The example string would put him into the group “seattle_production”.
User name (full name for display)¶
a
User name (full name for display)
b
displayname
c
LDAP attribute holding the user's (full) name
e-Mail address¶
a
e-Mail address
b
c
~
Only users with email address¶
a
Only users with email address
b
c
When checked only LDAP entries with a filled email address (attribute mail) are imported. To avoid import of guest and dummy accounts.
Automatic import¶
a
Automatic import
b
c
When activated users don't have to be imported in the backend. If a FE-user is successfully authenticated against the LDAP directory the user record in the database is imported/updated.
Use FEuser->BElogin¶
a
Use FEuser->BElogin
b
c
Ingmar Schlecht and Olivier Dobberkau provide an extension for synchronizing FE and BE users. When you activate this checkbox this extension is used to sync users automatically (extension Feuser->BElogin must be installed and loaded)
FAQ¶
- What is my base DN? In a W2k environment it should be the domain name.
- Which servers support the “memberOf/groupMembership” attribute? Win2k Active Directory and Novell e-directory definitely support this attribute.
- Why can I choose between two Active Directory modes and what is the difference? When authenticating against a Windows domain controller th “old” Windows NT syntax is domainuser, e.g. eumedianorman. With W2k the new format is user@domain , e.g. norman@myserver.local . In most cases it does not matter which format you choose but some users reported problems when using the wrong format.
- Users are imported but their password as I see it in the backend is wrong. Why? The passwords you see in the backend are created randomly. There is no import of passwords but authentication is done everytime against the LDAP server.
- Can I assign users to groups? Yes, currently standard implementations of AD, NDS and OpenLDAP are supported. Additionally you may define own attributes to build your usergroups.
- Can I import user groups automatically? Yes, you can.
- Can I encrypt my connection to the LDAP server? Yes, begin your server definition with “ldaps://”. The default setting for encrypted connections is port 636.You need to compile PHP with SSL support (or load the module under Windows).
- How does the SSO integration work? For single sign on the user's password is encrypted and cached, the key is stored in a cookie. Just tick the checkbox in the extension's settings.
Adminstration¶
This extension can only be accessed by administrators!
In the Backend you are able to import new users, to update existing ones or to delete users from the TYPO3 database which are not in the directory anymore. Theseork for both FE- and BE-users.
How authentication works¶
When a user tries to log on the extension passes the credentials to the LDAP server(s) and verifies them. When a LDAP server can authenticate the user he is logged on. When you tick the checkbox “Import users automatically” new users (in the directory but not in the TYPO3 database) are imported after authentication. Records of existing users are updated.
For new users imported from the directory random passwords will be inserted!
You may choose whether authentication is done only against your directory or also again the TYPO3 user database.
Known problems¶
LDAP support in PHP¶
When using the Windows Quickstart package, you have to do the following to get the extension working (otherwise you will receive a white screen when trying to import/update users):
Copy c:apachephpdllslibsasl.dll to C:WINNTSystem32
Uncomment the ldap line in php.ini (C:apachephpphp.ini)
BE-Login unencrypted¶
The extenson switches the settings for BE-Login to normal if the extension is used for BE authentication. Consider using HTTPS for the BE.
ChangeLog¶
Version 2.3:
- Support for encrypted (TLS) connections to LDAP servers.
- Integration with Single Sign On Extensions eu_sso_xxx.
Version 2.4:
- Removed NetBIOS SSO part.
- Using René Fritz's authentication service. Compatible with TYPO3 3.7 only.
Version 2.7:
- Compatible with TYPO3 3.7 and 3.8.
- Configuration changed.
 EXT: LDAP Integration - 5
EXT: LDAP Integration - 5