DEPRECATION WARNING
This documentation is not using the current rendering mechanism and is probably outdated. The extension maintainer should switch to the new system. Details on how to use the rendering mechanism can be found here.
EXT: naw_securedl¶
| Author: | Kasper Skårhøj |
|---|---|
| Created: | 2002-11-01T00:32:00 |
| Changed by: | Dietrich Heise |
| Changed: | 2013-10-23T09:50:48.647953183 |
| Author: | Dietrich Heise |
| Email: | typo3-ext(at)bitmotion.de |
| Info 3: | |
| Info 4: |
EXT: naw_securedl¶
Extension Key: naw_securedl
Copyright 2013, Dietrich Heise, <typo3-ext(at)bitmotion.de>
This document is published under the Open Content License
available from http://www.opencontent.org/opl.shtml
The content of this document is related to TYPO3
- a GNU/GPL CMS/Framework available from www.typo3.com
Table of Contents¶
EXT: naw_securedl 1
Introduction 1
What does it do? 1
Screenshots 1
Administration 2
Details on configuration evaluation 3
Backend Module 3
Known Limitations / ToDo 3
Introduction¶
What does it do?¶
In TYPO3, assets like PDFs, TGZs or JPGs etc. are normally just referenced by a URL e.g. to “fileadmin/...”. The file itself is delivered directly by the web server, and is therefore not part of the TYPO3 access control scheme – files remain unprotected, since URLs can be re-used, emailed, Google-included or even guessed.
The “naw Secure Download” extension (“naw_securedl”) changes this behavior: Files will now be accessed through a eID Script script that honors TYPO3 access rights. The converted URL's will then look like this:
index.php?eID=tx_nawsecuredl&u=1&file=fileadmin/secure/test.jpg&hash= 306a7839647a68caf24b50870a59d3fc
This works regardless of where the files come from, is not limited to special plugins etc.
Since in most cases you will not want to protect everything (which means that everything undergoes rather performance-consuming access right checking), naw Secure Download is highly configurable. You may choose:
- what directories to protect (e.g. you can include typo3temp or not,)
- what file types to protect (do you want to protect JPGs or not? etc.)
- what domains are considered local
As a complementary measure, you will of course need to configure your web server not to deliver these things directly (e.g. using .htaccess settings).
Screenshots¶
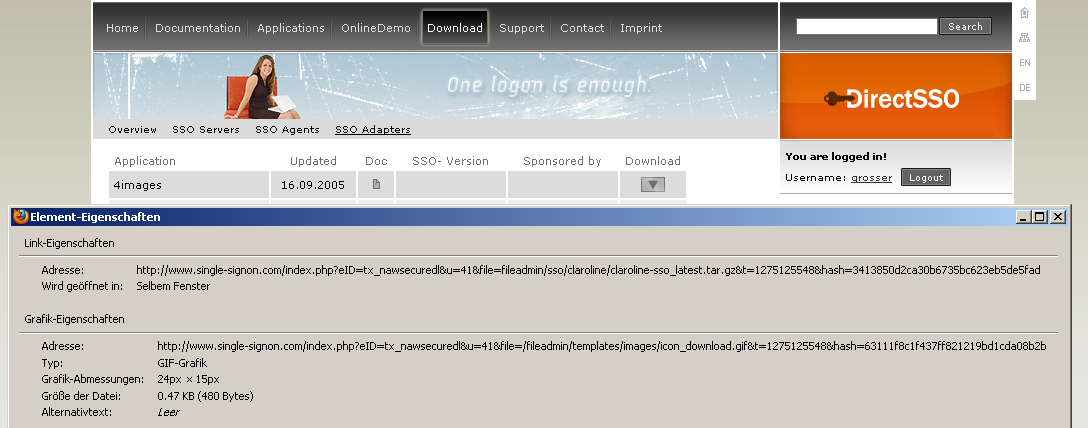 Picture 1 Secured File Download Example
Picture 1 Secured File Download Example
Administration¶
All configuration of this extension is made in the Extension Manager.
securedDirs¶
Configuration option
securedDirs
Description
List of directories of your TYPO3 Server in that files should be secured, separated by |
For exclude a sub-directory in a directory use (?!path/to/sub)path
filetype¶
Configuration option
filetype
Description
List of file types that should be secured, separated by |
forcedownload¶
Configuration option
forcedownload
Description
If this is checked some filetypes are forced to be downloaded in contrast of beeing embedded in the browser window
forcedownloadtype¶
Configuration option
forcedownloadtype
Description
List of filetypes that should be forced to be downloaded (see above)
domain¶
Configuration option
domain
Description
This is only required for absolute filelinks to your local server, e.g. “ http://my.server.com/fileadmin/image.jpg ” (instead of the normal internal link that reads “ fileadmin/image.jpg ”.) In other words: In most cases, this value can be left empty.
additionalMimeTypes¶
Configuration option
additionalMimeTypes
Description
Comma separated list of additional MIME types (file extension / mime type pairs, in which file extension and MIME type is separated by a pipe symbol). Can be used to override existing MIME type settings of the extension as well.
cachetimeadd¶
Configuration option
cachetimeadd
Description
The time that is added to the default or page cache, that the link to the secured element is valid.
debug level¶
Configuration option
debug level
Description
For developing only
log¶
Configuration option
log
Description
Each file access will be logged to database, this could be a performance issue, if you have a high traffic site. If you decide to turn it on, a backend module will be activated to see the traffic caused by user/ file
outputFunction¶
Configuration option
outputFunction
Description
Due to possible restrictions in php and php settings, you probably need to adjust this value. By default “readfile” is used to deliver the file. If this function is disabled in your php settings, you can try fpasstrugh. If you hav problems with php memory_limit and big files to download, you need to set this to readfile_chunked, which delivers the files in small portions. If you activate the logging, only the transmitted portions are stored in the database table. Again, make sure you have no performance problem here, because multiple SQL- queries are fired to track the transmitted bytes.
outputChunkSize¶
Configuration option
outputChunkSize
Description
Only applicable if you use readfile_chunked (see outputFunction). Specify the number of bytes, served as one chunk when delivering the file. Choosing this value too low is a performance killer.
linkFormat¶
Configuration option
linkFormat
Description
The Format for the link generated by naw_securedl. You can change this if you apply appropriate mod_rewrite rules in your .htaccess file.
Example:
linkFormat: securedl/###FEUSER###/###TIMEOUT###/###HASH###/###FILE###
Put the following in your .htaccess (one line)
RewriteRule ^securedl/([d]+)/([d]+)/([0123456789abcdef]+)/([^&]+)$ index.php?eID=tx_nawsecuredl&u=$1&t=$2&hash=$3&file=$4 [nc,L]
You also need to secure all the directories and filetypes by your server configuration. This can be done with .htaccess files. Some example .htaccess files you find in the /res folder.
Note: This extension cannot secure links to files that you include in your CSS file. For example you can secure /fileadmin with the default .htaccess_deny file by putting the file in /fileadmin. You can allow /fileadmin/templates/ with the default .htaccess_allow file by putting this file to /fileadmin/template/
Details on configuration evaluation¶
The first three config fields (securedDirs, filetype and domain) allow regular expressions, but with limitations because some characters (slash, backslash, dot, blank) are automatically quoted for your convenience.
For filetype (meaning actually the file extension), all upper/lowercase combinations are automatically included (e.g. “gif” would also cover “giF”.)
The | stands for “OR” .
Regex examples for securedDirs:
If for example you need to secure fileadmin and typo3temp, but not uploads:
fileadmin|typo3temp
To secure everything under fileadmin/secure or typo3temp, you need to write
fileadmin/secure|typo3temp
You also can group some elements with regular expression, but you should be carefull with grouping because the complex regex in the extension does not work if some other matches were output by the regex.
For grouping “ ( ) “ is used, but in our case you need to exclude the result of this ( ) . This can be done with (?: )
For example we need to find all under fileadmin/secure1 fileadmin/secure2 fileadmin/secure3 or typo3temp
fileadmin/secure(?:1|2|3)|typo3temp
for the same need you can use also [ ] but all chars between [ ] are allowed here
fileadmin/secure[123]|typo3temp
If you need to exclude some subfolders in a secured directory you can do this by (?! ) For example like
(?!fileadmin/unsecured)fileadmin
More information can be found here: http://www.regular- expressions.info
Backend Module¶
Since version 1.0.0 this extensions contains a backend module. With this module you can show the summerized download traffic by a given timeframe for all users or by a frontend user. Since version 1.2.0 you will see all files and filesizes downloaded by specified users.
Known Limitations / ToDo¶
- get a hook for showpic.php – currently, there is none (thus xclassing necessary)
- support for links from one PDF to another
- Allow optional advanced mode for full Regex support
- Images in Direct Mail newsletters, doesn't work correct with secure_dl :(
EXT: naw_securedl - 4