LDAP¶
The second tab is the global configuration about a single LDAP server.
Sections:
Server¶
Choose your LDAP type (OpenLDAP or Active Directory). This is used internally to follow (or not) referrals returned by the LDAP server and to help you with suggested mapping configuration.
Character set¶
Character set of your LDAP connection. Usually utf-8.
Host¶
Host of your LDAP. You may use either a host name / IP address or prefix it with a protocol such as
ldap://<hostname> or ldaps://<hostname> (latter in case you want to connect with SSL).
TLS¶
Whether you want to use TLS, that is typically start with an connection on default port 389 and then set up an encrypted connection.
Note
More information on TLS may be found at http://www.openldap.org/doc/admin24/tls.html.
SSL¶
Whether you want to use SSL, that is start with an encrypted connection on default port 636.
Note
Some web servers may fail at connecting to the LDAP server since they report that the server certificate is
untrusted (although issued by a valid CA such as Letsencrypt). In case this happens and you cannot change the web
server configuration (e.g., shared hosting), you may add this line to typo3conf/AdditionalConfiguration.php:
// Always trust the LDAP server certificate
putenv('LDAPTLS_REQCERT=never');
Bind DN¶
DN of the LDAP user you will use to connect to the LDAP server. The DN is composed of a series of RDN’s which are the unique (or unique’ish) attributes at each level in the DIT. The following diagram illustrates building up the DN from the RDN’s.
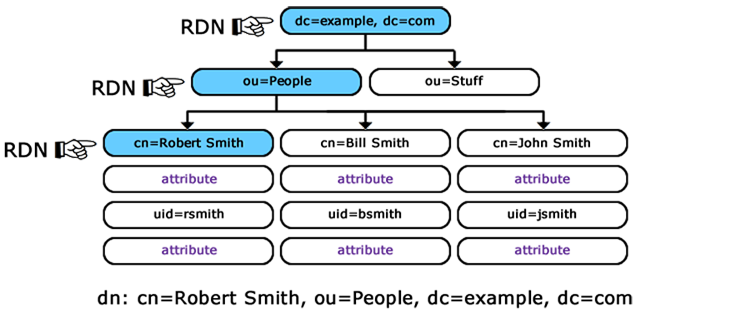
Building up the DN (Distinguished Name) from the RDN’s (Relative Distinguished Names)
Example:
cn=Robert Smith,ou=people,dc=example,dc=com
Note
Your LDAP user needs to be granted access to the directory where users and groups are stored and full read access to users and groups for all attributes you plan to fetch.
When connecting to an Active Directory, this corresponds to a user account that has privileges to search for users.
E.g., CN=Administrator,CN=Users,DC=mycompany,DC=com. This user account must have at least domain user
privileges.
