DEPRECATION WARNING
This documentation is not using the current rendering mechanism and is probably outdated. The extension maintainer should switch to the new system. Details on how to use the rendering mechanism can be found here.
OpenLDAP / macmade.net¶
| Author: | Kasper Skårhøj |
|---|---|
| Created: | 2002-11-01T00:32:00 |
| Changed: | 2005-11-22T15:42:13 |
| Email: | macmade@gadlab.net |
OpenLDAP / macmade.net¶
Extension Key: ldap_macmade
Copyright 2000-2002, , <macmade@gadlab.net>
This document is published under the Open Content License
available from http://www.opencontent.org/opl.shtml
The content of this document is related to TYPO3
- a GNU/GPL CMS/Framework available from www.typo3.com
Table of Contents¶
OpenLDAP / macmade.net 1
Introduction 1
What does it do? 1
About 1
Users manual 2
Installation 2
Creating a new OpenLDAP server 2
Managing LDAP and Typo3 users 5
Known problems 6
To-Do list 6
Changelog 6
Introduction¶
What does it do?¶
This extension allows you to import and authenticate Typo3 users (frontend & backend) from OpenLDAP servers. You can also synchronize the LDAP users with any other database table. All the mapping process is done visually, through flexforms.
About¶
I decided to write this extension a long time ago, after having tested the existing LDAP extensions. The first goal was to simplify to configuration and the mapping process, by using dynamic flexforms sections, and to improve the usability of the import process.
This extension can only be used with OpenLDAP servers, and I don't plan to add support for other kind of LDAP servers.
If you're a Typo3 developer, and if you like the way the mapping is done, just feel free the take my code. It's here to serve. ; )
Users manual¶
Installation¶
The installation of this extension is very simple. Just connect to the Typo3 Extension Repository and download «OpenLDAP / macmade.net» (ldap_macmade), located in the backend module section. Note that you will also need to download the «Developer API» extension (api_macmade), as it will be needed by the plugin.
This extension is only available for Typo3 3.8 and greater, as it depends on the «sv» extension, included by default since Typo3 version 3.8.
When you install the extension, you'll notice two checkboxes.
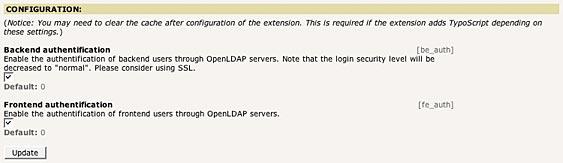
Those options control the authentication features. The first one allow the use of OpenLDAP servers for backend authentication, and the second one is used for frontend authentication.
If you don't allow those features, you won't be able to define an OpenLDAP server as an authentication source later.
Note that if you enable backend authentication, the login security level will de decreased to «normal». That means that the password of the backend users will be sent as clear-text. So consider using SSL for the Typo3 backend if you enable this feature.
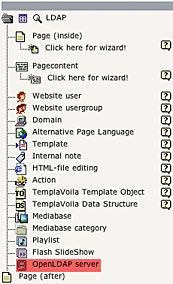
Creating a new OpenLDAP server¶
The next step is to create a new OpenLDAP server. On a sysfolder, just create a new element and choose «OpenLDAP server» from the list:
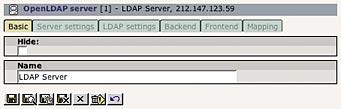
You'll then need to configure the OpenLDAP server. In the first tab, just enter a name for the server:
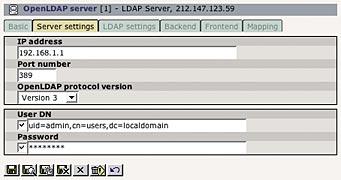
On the second tab, enter the server's informations, such as the IP address, LDAP protocol version, the username and password for LDAP operations, etc.:
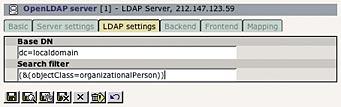
On the third tab, you'll have to enter the LDAP base DN, and a search filter to get LDAP users:
The fourth tab controls the backend users import process:
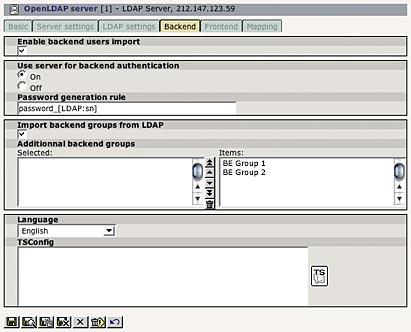
You can enable/disable backend users importation, and decide if you want to use that server as an authentication source (only if it has been activated in the extension manager). Note that you can use several servers for authentication.
You can also decide to generate an password for each imported backend user (of course, it's useful only if you don't authenticate the users directly through LDAP). You can dynamically use a field from the LDAP to generate the password. For instance, if you set this value to «password_[LDAP:sn]», the string [LDAP:sn] will be substituted by the «sn» field of the current user. With this feature, you can assign a different password for each imported user.
You can also decide to automatically import backend groups from the LDAP server and/or to add fixed existing backend groups.
The two last options control the language for the backend users, and their TSConfig.
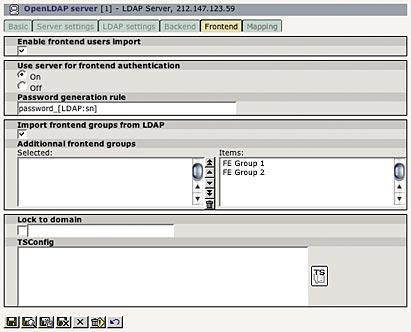
The fifth tab contains similar options, but this time for frontend users:
The last tab is certainly the most import one. It controls the mapping of the fields between the LDAP server and Typo3. This process is done visually, so it's very easy to use and understand:
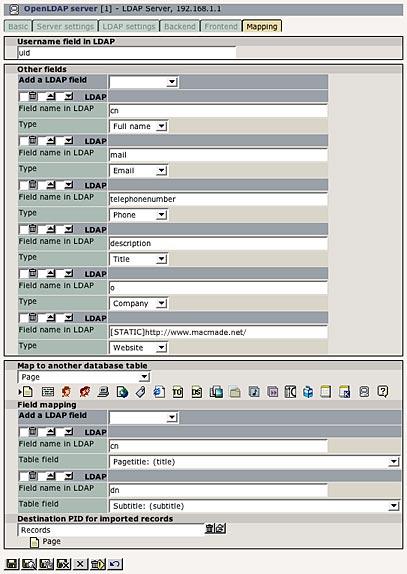
In the first field, you'll have to enter the LDAP username field. It will be used for Typo3 usernames.
You can then add as many other fields as you want. Each time, it creates an input field, and a selector box. Just enter the LDAP field on the input, and choose the type of field in the selector box. It will then automatically be mapped in Typo3 tables.
The last section allows you to synchronize LDAP users with another database table. You'll first have to choose which table to use, and then map the LDAP fields with the Typo3 table fields, displayed in the selector boxes. You can also choose a destination page for the imported records.
In the screenshot, we decided to sync LDAP users with the «Pages» table. It means that for every imported LDAP users, a new page will be created, with the fields specified in the mapping.
Managing LDAP and Typo3 users¶
To manage LDAP and Typo3 users, just open the OpenLDAP module, in the left menu of the Typo3 backend:
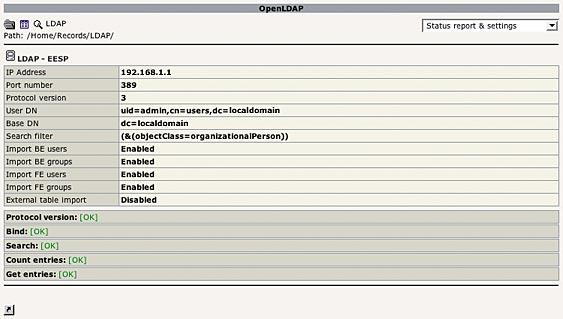
You'll first see a resume of your LDAP settings, with the status of the LDAP connection:
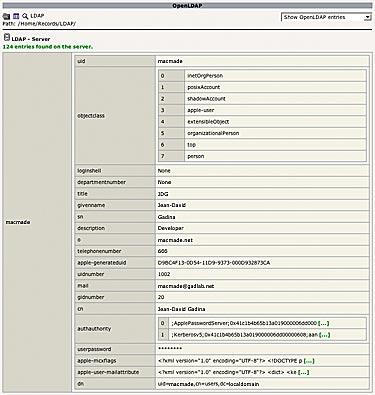
From here, you can also browse the LDAP entries:
If your settings are fine, you can then launch the users import process:
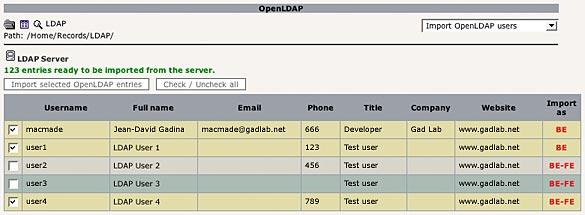
Just select the LDAP users you want to import, and click the «Import» button. The same process can be done to refresh Typo3 users data from the LDAP server:
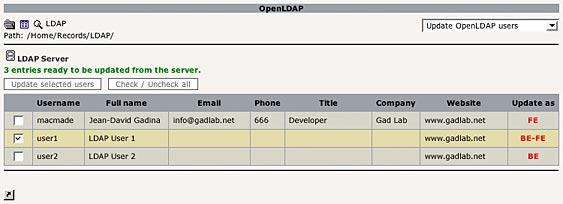
Known problems¶
None at the time. Just contact me if you find some.
To-Do list¶
- Add functionalities to delete Typo3 users who aren't present in the LDAP server.
- Find a way to crypt backend password. Any suggestion is welcome.
- I don't plan to support other types of LDAP servers, but if you're interested to add that kind of feature, just drop me a line.
- Please contact me if you have any suggestion about this extension.
 OpenLDAP / macmade.net - 6
OpenLDAP / macmade.net - 6