DEPRECATION WARNING
This documentation is not using the current rendering mechanism and is probably outdated. The extension maintainer should switch to the new system. Details on how to use the rendering mechanism can be found here.
EXT: Shibboleth Authentication¶
| Author: | Richard Rode |
|---|---|
| Created: | 2013-11-13T16:17:38 |
| Changed by: | Richard |
| Changed: | 2014-06-05T07:45:09 |
| Classification: | shibboleth_auth |
| Description: | Enables the single sign-on based on Shibboleth for frontend and backend authentication. |
| Keywords: | single sign-on, authentication, shibboleth |
| Author: | Tamer Erdogan |
| Email: | typo3@univie.ac.at |
| Info 3: | |
| Info 4: |
EXT: Shibboleth Authentication¶
Extension Key: shibboleth_auth
Copyright 2011, Tamer Erdogan
This extension is currently maintained by Richard Rode, Computer Center of the University of Vienna:<typo3@univie.ac.at>http://zid.univie.ac.at/.
This document is published under the Open Content License
available from http://www.opencontent.org/opl.shtml
The content of this document is related to TYPO3
- a GNU/GPL CMS/Framework available from www.typo3.com
Table of Contents¶
EXT: Shibboleth Authentication 1
Introduction 2
What does it do? 2
Screenshots 2
Users manual 3
Installation 3
Using the frontend login 3
Adding CSS 4
Using the backend login 4
Administration 5
How authentication works 5
Credits 5
Known problems 5
ChangeLog 5
Introduction¶
What does it do?¶
This extension enables the single sign-on based on Shibboleth for frontend and backend authentication. Apache's Shibboleth module has to be installed on the web server before you can use this extension.
Screenshots¶
Users manual¶
Installation¶
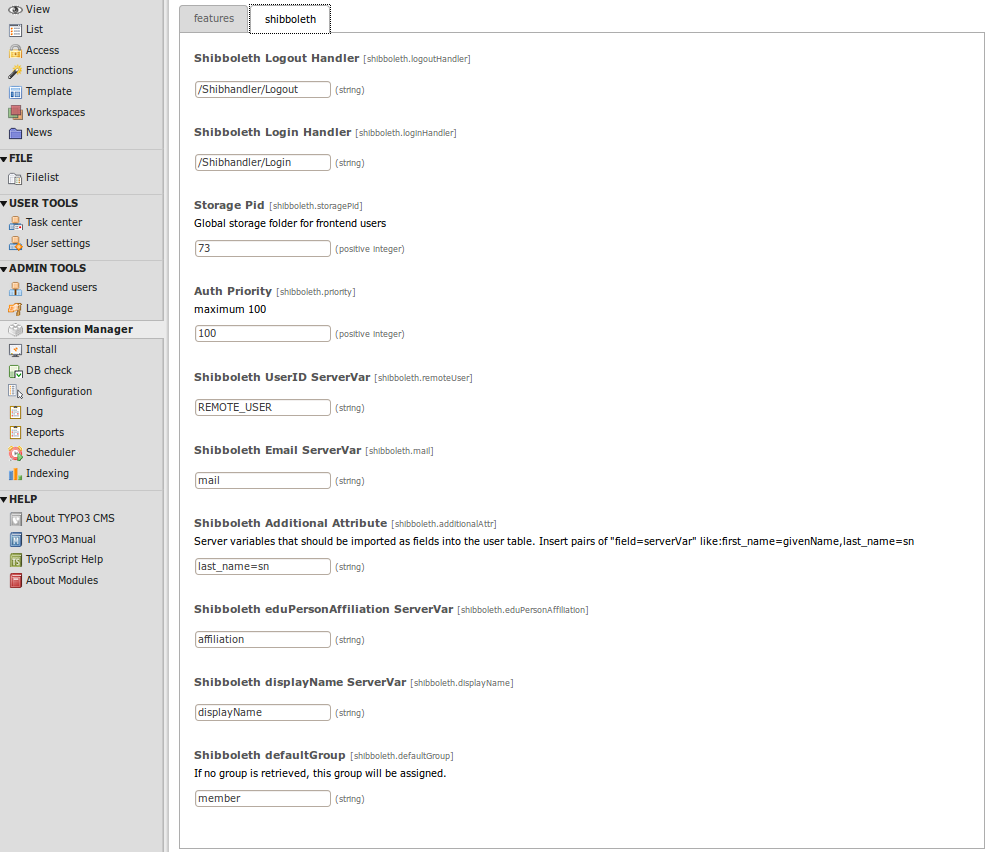
For frontend login you need a TYPO3 folder to store the users. So create one first and remember the id. After installing the extension with TYPO3's extension manger you have to activate the basic features in the extension's settings. The default settings prevent the extension to do anything! Shibboleth authentication can be activated for frontend and backend separately. It is highly recommended to keep a browser window with a logged in admin user open before activating and testing the backend login (see below). Otherwise you could lock yourself out, if your Shibboleth configuration didn't work.
The following htaccess rules must be added to the htaccess file in the TYPO3 root directory:
AuthType Shibboleth
ShibRequireSession Off
Require Shibboleth
In addition, if you have the RealUrl extension installed, the following line must be added to the htaccess file:
RewriteRule ^(Shib.*)/ - [L]
This has to be the first rewrite rule in your htaccess file.
You should try frontend login first. So insert the id of your new storage folder into the field “Storage Pid” and activate frontend login with auto import. The “Auto Import” option will create an entry in fe_users for every user who logs in. You will also find Shibboleth's affiliations imported as website user groups in this folder. You can manipulate the relation between affiliation names and group names with regular expressions. Use eduPersonAffiliationRegExPattern and eduPersonAffiliationRegExReplace for this. If you want to remove deprecated group assignments (i.e. affiliations that are no longer assigned to the user) check onlyAffiliationGroups too. Otherwise manual assignment of additional groups is possible.
To test your settings insert the frontend plugin on a test page (see below).
Using the frontend login¶
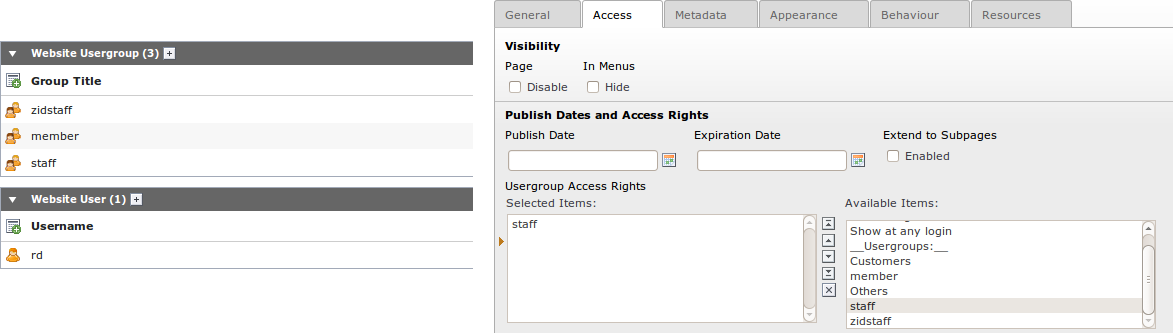
To activate the frontend authentication a plugin is available to the editors. Pages with the plugin as content element check if there is an already logged in frontend user available (no matter if logged in via Shibboleth or TYPO3's felogin). If yes, the status of this user is shown, if not, a redirect to the login mask of your ShibHandler's identity provider is set. Just like other logins in TYPO3 the plugin itself provides the login, not the protection. If you want the access to the content of your login page restricted, you have to assign the related group in the access settings. Do not assign any restrictions to the Shibboleth plugin itself! Otherwise no login redirects will be made.
The plugin itself has two options:
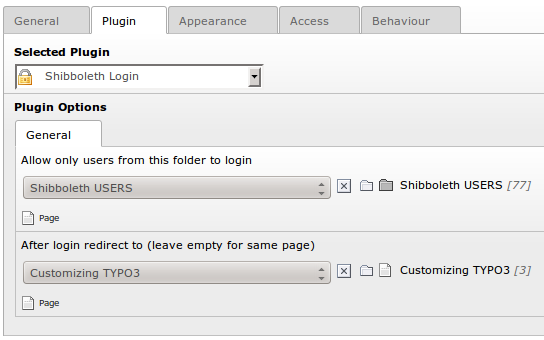
The first one allows the editor to restrict the access to special users. Just create a folder with website users and a user group. Set the access of your pages and content elements to this user group. Make sure that the user names correspond to the user names of the Shibboleth login. This option overrules the “Auto Import” in the extension's global settings (see below). No users will be imported, only the groups from the Shibboleth affiliations will be assigned to the users when they log in.
The second option performs a redirect after login. Leave this empty if you want to show the login page itself.
Adding CSS¶
Most of this extensions functionality consists of handling server variables and redirects. The only frontend output is a little form with your status. Their is no CSS for these elements as most of you might have these settings included in your standard CSS. If not, adding the following lines could help:
form.tx_shibbolethauth_pi1 {background: none repeat scroll 0 0 #EEEEEE;border: 1px solid #999999;padding: 6px;}
form.tx_shibbolethauth_pi1 fieldset {border: 1px solid #999999;padding: 10px;}
div.tx_shibbolethauth_pi1_error {background: #EEEEEE;border: 4px double #ff9999;padding: 10px;}
Using the backend login¶
For security reasons backend users are not imported automatically. So before you start to activate the backend login, go to the root folder of your TYPO3 installation, create a user with the username of an existing Shibboleth account and give it admin rights. Go back to the extension manager, open the settings of the Shibboleth extension and activate the backend login and the option “Only Shibboleth Backend”. Do not close the window! Open another browser (for example Firefox and Chrome as shown in the screen shot) and try to login with the former created Shibboleth user.
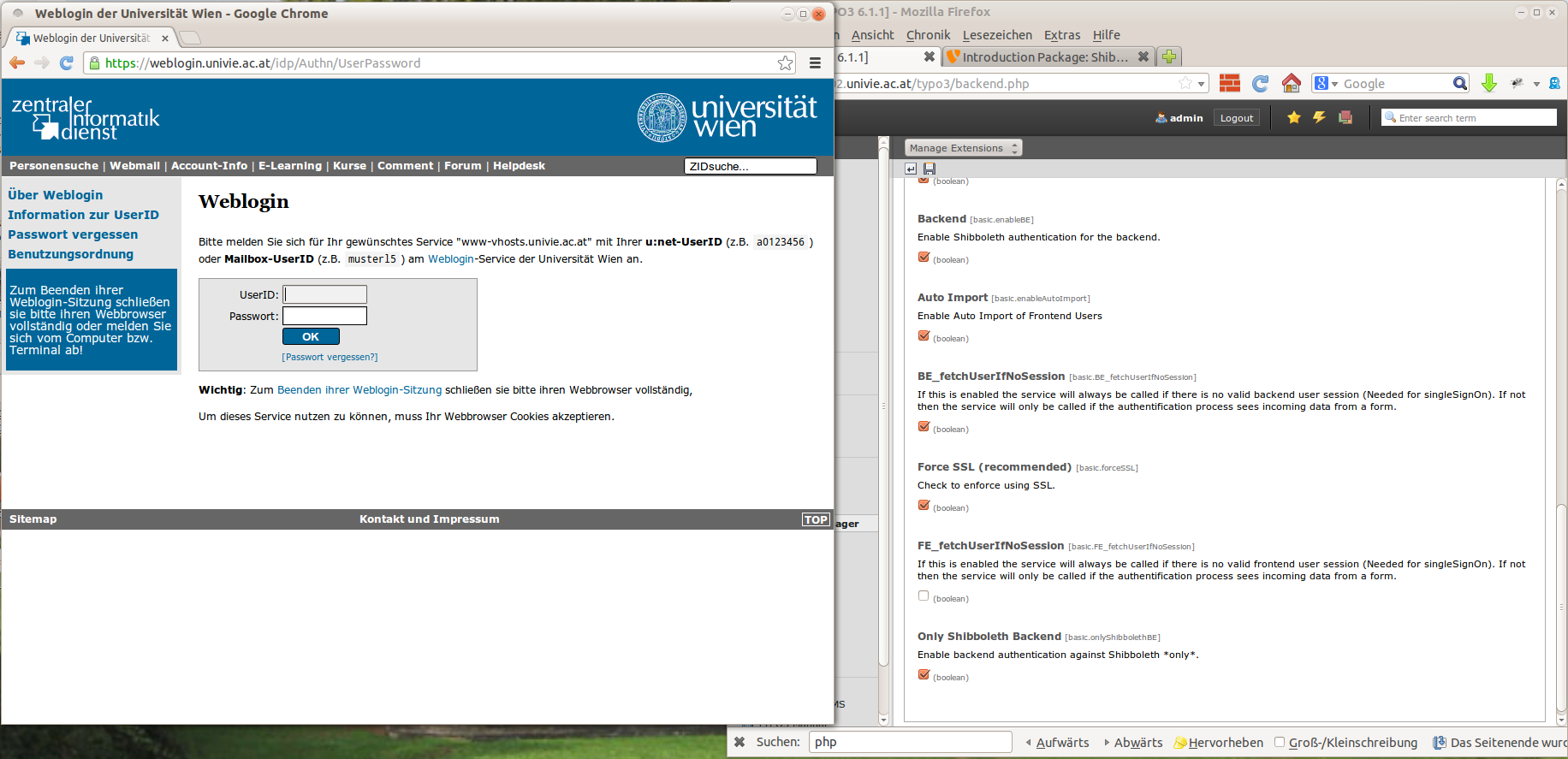
After successful login you can close the other browser. Having Shibboleth's backend login enabled as described above you will never be able to login with a normal TYPO3 account again. Insecure extensions which allow SQL injection could not be misused to read the password hash of one of your admin users, because these passwords will never work again. Therefore Shibboleth authentication brings an increase of backend security against hacker attacks.
The extension should be able to handle session timeouts. Therefore the configuration variable showRefreshLoginPopup is set to open the login form in a new window. Keep in mind that TYPO3's refresh login does not work in debug mode. As the life time of your login depends on the Shibboleth sever variable it is recommended to set TYPO3's session timeout to a higher value if problems with the refresh login occur.
Administration¶
The settings are accessible in the extension manager as described above and can only be accessed by administrators (see installation).
How authentication works¶
Shibboleth is a single sign-on technology, that allows you to access the protected content of one or more service providers by logging in at an identity provider. This is implemented via redirects and server variables provided by the web server's Shibboleth module. When the user tries to access protected content, TYPO3 looks if there is an existing fe-user or special evironment variables with the user's data. If not, it redirects to a directory (= ShibHandler) protected by the Apache's Shibboleth module. This will send the browser to the assigned identity provider with the login page. After logging in the browser gets redirected to the TYPO3 page again, where the php script can now read the server variables with the user's data. The authentication and the environment variables are not provided by this extension! TYPO3's Shibboleth authentication needs an installed shibboleth module on your web server!
Credits¶
Thanks to all of you who gave feedback. Bug reports and feature requests are always appreciated. Please write to typo3@univie.ac.at .
Special Thanks to Stefano Beriozza for the Italian language pack.
Known problems¶
None so far.
ChangeLog¶
2.6.2: Added option onlyAffiliationGroups: Manually added or deprecated group assignments will be removed if user misses according affiliation.
2.6.1: Fixed session timeout behaviour with showRefreshLoginPopup.
2.6.0: Added regex variable to settings to change affiliations before creating FE groups. Compatibility for 6.2.
2.5.7: Bugfix: Set additional attributes at import. Name of config variable corrected in ext_conf_template.txt.
2.5.6: Storage folder for individual groups. Redirect option. Italian language pack. Shibboleth plugin seperated from felogin functionality.
2.5.5: Better manual. Clean up of language files. Settings for additional attributes and default group. Manually assigned groups for fe-users won't be overwritten.
2.5.3: $_SERVER['AUTH_TYPE'] in capital letters is accepted.
2.5.2: Access of methods changed from private to protected.
2.5.1: Small bugfix in onlyShibbolethFunc.
2.5.0: BeUser not found handling correction.
2.4.4: SSL check with TYPO3 functions.
2.4.3: Password is improved with md5.
2.4.2: Realurl Bugfix. Apache mod_rewrite adds REDIRECT_ prefix in SERVER Vars.
2.4.1: TYPO3_cliMode bugfix. Cli users should not be authenticated with shibboleth auth.
2.4.0: Only Shibboleth Backend Configuration: Enable backend authentication against Shibboleth only.
2.3.0: Security update: forceSSL configuration added.
2.2.1: Small change in getFEUserGroups hook .
2.2.0: New hook for getFEUserGroups.
2.1.0: fe_user auto import bugfixes.
2.0.0: The first stable version.
 EXT: Shibboleth Authentication - 5
EXT: Shibboleth Authentication - 5